Alright, everyone, let’s talk about something we all take seriously but sometimes don’t think enough about: keeping our crypto safe.
Now, if you’ve ever worried about losing your private keys or had nightmares about a rogue team member draining the DAO treasury, this post is for you. On Monday this week I presented this very topic to a local community of crypto enthusiasts and the feedback I received was great and people engaged, asked questions and it really made my day. I have to thank Clarissa P. from Algarve Blockchain Community (ABC- check it out and maybe join some of their events in the Algarve) for organising but also for being a friend and giving me the stage to share my knowledge with others.
We’re diving into signatures vs multisig—a showdown between simplicity and security. We’ll unpack what they are, when to use them, and how not to overcomplicate your life in the process. By the end, you’ll not only know the difference but also have some real-world tips to apply straight away. And yes, we’ll get hands-on, so prepare to watch a short video on how to setup a simple multisig on Gnosis.
Let’s get into it!
What’s the difference between a digital signature and a digital wallet?
Let's start by making sure we are all on the same page and we understand one major difference between a digital wallet and a digital signature.
A digital WALLET is an electronic application that stores payment information, enabling secure online and mobile transactions without physical cash or cards. It can hold payment methods, loyalty cards, and digital IDs, focusing on convenient and protected financial interactions.
A digital SIGNATURE by contrast, is a cryptographic technique that verifies the authenticity and integrity of digital documents, messages or transactions in our case. Using complex mathematical algorithms and public keys, digital signatures create a unique electronic "fingerprint" that confirms the sender's identity and ensures the transaction hasn't been altered.
What is a digital signature?
Crypto single signatures and multisig (multi-signature) are both security measures used in cryptocurrency transactions, but they serve different purposes and operate in distinct ways.
Let's break them down using simple analogies:
Single signatures
Imagine you're sending a letter to a friend. To prove it's really from you, you sign it with your unique signature. In the crypto world, this is what a digital signature does. When you make a cryptocurrency transaction, you "sign" it with your private key. This signature proves that you, the owner of the funds, authorised the transaction. It's like having a super-secret password or handshake that only you know.
Here's how it works:
1. You have a private key (your secret handshake) and a public key (your public identity).
2. When you want to send crypto, you use your private key to create a unique signature for that specific transaction.
3. Anyone can use your public key to verify that the signature is valid, but they can't figure out your private key from it
MULTISIG (Multi-signature)
Now, let's say you have a valuable asset stored in a super secure vault/safe. Instead of using just one lock, you decide to use multiple locks for extra security. This is essentially what multisig does for cryptocurrency wallets.
In a multisig setup:
The wallet has multiple "locks" (private keys). To open the "vault" (make a transaction), you need a certain number of these keys, but not necessarily all of them.
For example, in a 2-of-3 multisig wallet: there are three key holders, and any two of them must agree to make a transaction. It doesn’t matter in what order as long as two of them sign that transaction. It's like having a safety deposit box at a bank that requires both your key and the bank manager's key to open.
In conclusion, the purpose of each is:
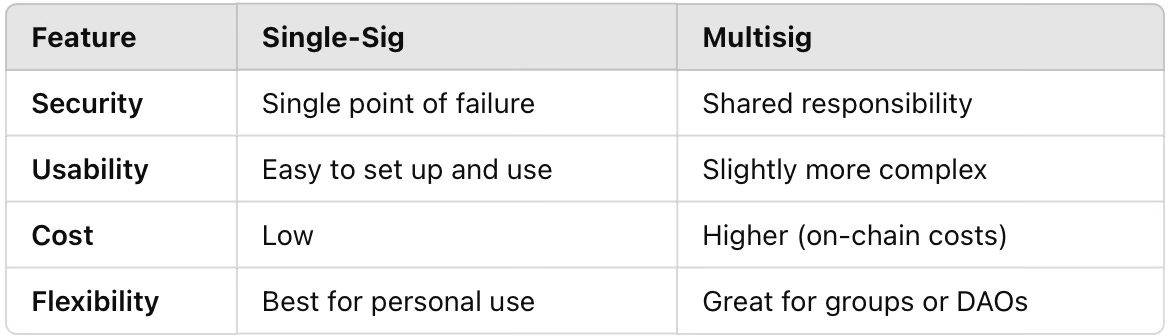
Single signatures prove ownership and authorise individual transactions. Like a personal seal or signature. Use one private key. Used in every transaction.
Multisig add an extra layer of security by requiring multiple approvals. Involves multiple keys. Often used for shared wallets or high-security storage.
Watch a short video on a simple 2 out of three multisig setup 👇👇
Multisig use cases
Multisig wallets have numerous real-life applications, enhancing security and control in various scenarios.
Corporate treasury management: Companies require multiple executives to approve fund transactions using multisig, reducing the risk of internal fraud.
Escrow services: Multisig enables trustless escrow systems, where a neutral third-party arbitrator can step in to ensure fair resolutions between buyers and sellers.
Decentralized autonomous organizations (DAOs): DAOs manage treasury funds through multisig wallets, ensuring that no single member can act independently to control funds.
Crypto inheritance planning: Multisig allows trusted family members or friends to hold additional keys, providing a secure way to recover funds in case of unexpected events.
Crowdfunding and fundraising: Multisig protects campaign funds by requiring multiple stakeholders to approve transactions, ensuring transparency and accountability.
Secure long-term storage (cold storage): Users can distribute keys across multiple locations or trusted individuals to add layers of security to their long-term crypto holdings.
Non-profit or charity fund management: Multisig ensures that spending decisions in charities or non-profits are approved by multiple trustees, promoting accountability and transparency.
Trustless loan contracts: Borrowers and lenders can create secure collateral arrangements using multisig, with a neutral third party involved to resolve disputes if needed.
Multi-party payment channels: Multisig is a key feature of the Lightning Network, enabling secure and efficient off-chain transactions.
Joint bank accounts: Couples or partners can use multisig wallets to prevent unilateral spending from shared accounts, ensuring mutual agreement on all transactions.
Benefits, drawbacks and risks in using single-sig or multisig
Public and private key security faces several common threats:
Social engineering: Hackers trick people into revealing their private keys or passwords, often through phishing emails or fake websites.
Team member collusion: Dishonest employees or insiders share or misuse private keys, putting the organisation’s data and funds at risk.
Quantum computing: Future quantum computers could potentially break current encryption methods, making today’s keys vulnerable to being cracked.
Man-in-the-middle attacks: Hackers intercept and change the communication between two people, letting them spy on or manipulate data.
Brute-force attacks: Hackers try every possible key combination until they guess the correct one, which works if the keys are weak or too short. In reality this was a real threat before 2013 when most people use to set their own private keys manually, using the seed words, etc. Nowadays, private keys are automatically generated making this a lower risk.
Key theft: If hackers steal the keys, they can access private information. For example, in the 2022 LastPass breach, hackers got hold of credentials and keys to unlock stored data.
Improper key management: This happens when keys are stored carelessly, like keeping them in the same place as the data they protect, making it easy for hackers to steal both.
How are multisig wallets used today
According to Chainalysis, approximately $2.2 billion worth of cryptocurrency was stolen in 2024, representing a 21.07% increase from 2023.
BITCOIN multisig adoption: The adoption of multisig wallets has seen remarkable growth in the Bitcoin ecosystem. As of January 2025, over 20% of Bitcoin wallets are estimated to be multisig. This represents a significant increase from 15% in 2022, indicating a growing adoption of multisignature technology for enhanced security in cryptocurrency storage and transactions.
LIGHTNING NETWORK utilises multisig as a fundamental component for off-chain transactions, enabling secure and efficient micro-payments.
GNOSIS Safe: Widely adopted by decentralized autonomous organizations (DAOs) and individual users, Gnosis Safe is a leading multisig wallet known for its robust security features. As of now, there have been no reported security breaches involving Gnosis Safe.
BITGo: A prominent digital asset custody provider, BitGo offers multisig wallet services to institutional clients, ensuring that multiple approvals are required for transactions. BitGo has maintained a strong security record without known hacks.
ELECTRUM Wallet: A popular Bitcoin wallet, Electrum supports multisig configurations, allowing users to set up wallets that require multiple signatures for transactions. Electrum's multisig feature has been reliable, with no significant security incidents reported.
Examples of previous crypto hacks due to misuse use of multisig wallets and private keys
RONIN Hack (March 2022)
The Ronin Network, tied to the popular game Axie Infinity, suffered a $625 million hack, one of the largest in crypto history. Ronin used a 5-out-of-9 multisig wallet for transaction approvals. This means 5 signatures were needed to validate a transaction.
Hackers gained control of 5 private keys, giving them enough signatures to approve large withdrawals. They achieved this through social engineering attacks and exploiting weak security in validator nodes.
The multisig was heavily centralised, with multiple keys managed by related parties (Sky Mavis employees and partners). This made it easier for hackers to compromise enough keys. The hack exposed flaws in relying on centralised control for multisig wallets, emphasizing the need for decentralisation and better key management practices.
RADIANT Capital Hack (September 2023)
Radiant Capital, a DeFi protocol, suffered a $1.1 million hack due to a vulnerability in its multisig implementation. The protocol used a multisig wallet to manage funds, requiring approval from multiple parties. However, attackers found a way to manipulate the withdrawal process through an unprotected function.
Radiant’s multisig didn’t enforce strict checks on who could call sensitive contract functions. The hackers exploited this by submitting a malicious request that passed the multisig’s verification process. Funds were drained, and the event highlighted the need for code audits and tighter multisig restrictions to avoid trust in the wrong entities.
Current trends in managing crypto security with multisig
A growing number of crypto projects are setting up multisig wallets and assigning signature responsibilities to community influencers, trusted third parties, or external stakeholders, rather than keeping it within the core team (employees, founders, or partners).
For example, in late 2021, SushiSwap, a prominent decentralised exchange, revamped its multisig governance by involving community influencers and DeFi leaders as signers. SushiSwap’s multisig wallet required multiple approvals for executing transactions, such as moving treasury funds.
They added external, trusted figures from the broader DeFi ecosystem, like prominent protocol developers and community members, to the signing group. This move reassured the community during a period of leadership disputes, demonstrating a clear push toward decentralisation.
CHALLENGES
Coordination: external signers may not respond quickly, slowing critical operations.
Accountability: influencers might lack the technical expertise or accountability mechanisms to handle such responsibility properly.
Trust transfer: while moving responsibility to community members, the reliance on the influencers’ integrity becomes a new potential risk.
When to choose a multisig solution for you or your project
When setting up a multisig wallet, start by determining the optimal number of participants needed for your use case. This decision depends on the purpose of the wallet and the level of security you require. It’s also important to consider the technical expertise of all wallet managers, as those involved should be comfortable with the process to avoid mistakes or delays.
Keep in mind that multisig wallets may result in slower transaction speeds and higher fees compared to single-signature wallets, so weigh these factors against your security needs. For advanced users, evaluating smart contract integration can be beneficial, as it allows for programmable security rules that enhance control and functionality.
Additionally, ensure the wallet you choose supports the specific cryptocurrencies or tokens you plan to store. Selecting a reputable wallet provider with a strong security track record is equally essential to minimise risks. Lastly, evaluate the wallet’s backup and recovery mechanisms to prepare for key loss scenarios, ensuring you have a reliable way to regain access to your funds if needed.
When implementing a multisig wallet, start by assessing your security needs based on the value of your assets and potential risks. This evaluation will help you choose an appropriate signature threshold, such as 2-of-3 or 3-of-5, to strike the right balance between security and convenience. For added protection, consider integrating hardware wallets, as they provide a more secure way to store private keys.
To further reduce risks, plan for the geographical distribution of keys, which can help mitigate physical risks like theft or natural disasters. Using hardware wallets from different manufacturers is also a good practice to avoid dependency on a single vendor, which can create vulnerabilities. Finally, implement robust recovery options to address key loss or compromise, ensuring you can access your funds even in unforeseen circumstances.
Using multisig for individual needs: If you have a lot of Bitcoin (or other assets) or just want extra security, a multisig wallet can be a great option. It works like needing more than one key to open a safe—so even if one key is lost or stolen, your Bitcoin stays safe. This makes it ideal for protecting large amounts of Bitcoin, sharing access with trusted people, or planning for emergencies like inheritance. It’s also helpful if you want to spread the keys across different devices or places to make things even more secure.
Addressing the quantum computing “elephant” in the room
Cryptocurrencies like Bitcoin and Ethereum rely on strong encryption to keep your funds safe. They use methods like public key cryptography, Eliptic Curve Digital Signature Algorithm (ECDSA) and hash functions (like SHA-256) to protect transaction data. The security behind these systems comes from how hard it is for regular computers to solve certain complex math problems, like guessing a private key from a public one. Quantum computers, however, are a different kind of machine that could eventually crack these protections.
How could quantum computers break crypto?
Quantum computers use special algorithms to solve problems much faster than regular computers. For example:
Shor's algorithm: Could break ECDSA by figuring out private keys from public keys.
Grover's algorithm: Helps speed up guessing hashes but is less of a threat compared to Shor's algorithm.
For a quantum computer to actually crack a private key, a few things need to happen:
Your public key must be visible: Once you’ve made a transaction, your public key is published on the blockchain. A quantum computer could use this to figure out your private key.
Quantum computers must get much stronger: It would take millions of stable qubits (quantum bits) to break encryption like this. The best quantum computer today (e.g., Google’s Willow chip) has only 105 qubits, which is still far from what's needed.
Unused addresses are safe: If you haven’t used an address yet (haven’t signed any outgoing transactions, or transferred funds), its public key isn’t visible, so it can’t be targeted by quantum algorithms.
Right now, quantum computers aren’t powerful enough to break the encryption that cryptocurrencies use, and it could still take many years for them to reach that level. This gives blockchain developers time to upgrade to quantum-resistant systems, like new types of encryption that quantum computers can’t crack.
How can you protect yourself?
Don’t reuse addresses: If you use a fresh address for every transaction, your public key won’t be exposed repeatedly.
Be ready for upgrades: Keep an eye out for when cryptocurrencies start adopting quantum-resistant technologies and make sure you switch to those systems.
Quantum computing isn’t a threat yet, but it could be in the future. Developers are already working on ways to stay ahead of the game, so as long as you stay informed, your funds should remain safe.
Thanks for reading a rather longer post, and if you have any questions, don’t hesitate to leave them in the comments.



Loving the letter! You are doing so well!